- Microsoft has spotted a new phishing attack vector in the wild
- Storm-2372 is stealing access tokens through Microsoft Teams
- The group has been linked to Russia with medium confidence
A new phishing campaign has emerged that utilizes ‘device code phishing’ tactics through Microsoft Teams, targeting various organizations including governments, NGOs, and private industries across Europe, North America, Africa, and the Middle East. This sophisticated approach has been detected by Microsoft, which warns that the attackers leverage Teams video conferencing invitations. These invitations prompt victims to enter a device code generated by the attacker, leading to the unauthorized acquisition of valuable access tokens, effectively granting the attackers access to victims’ emails and sensitive data.
Table of Contents
Data theft and lateral movement
According to Microsoft, Storm-2372, the threat actor behind this campaign, initiates contact with victims through messaging platforms such as WhatsApp, Signal, and Microsoft Teams. They build a rapport with the victim, presenting themselves as influential figures within the victim’s industry. After establishing trust, the attacker invites the target to an online meeting, where they are prompted to complete a device code authentication request.
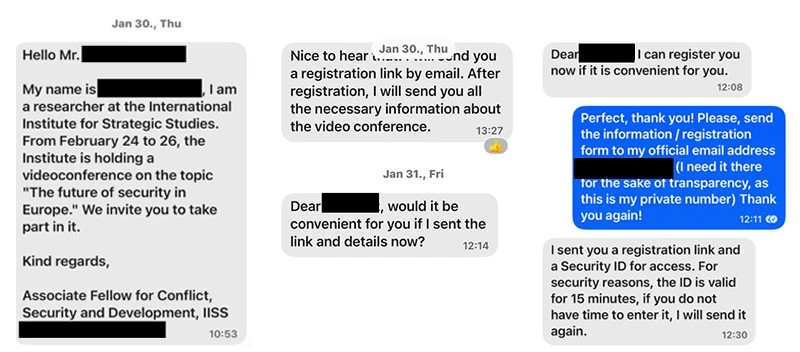
The attacker generates a legitimate device code authentication request and sends the code to the victim, who unwittingly enters it into a legitimate authentication service page. This action enables the attacker to capture access and refresh tokens, thereby maintaining control over the compromised account.
Once access is gained, attackers often attempt to move laterally within the victim’s network. They perform keyword searches in messaging services to harvest sensitive information, including usernames and passwords, as well as data related to administrative accounts, remote access applications like TeamViewer and AnyDesk, and other confidential keywords pertinent to government and ministry operations.
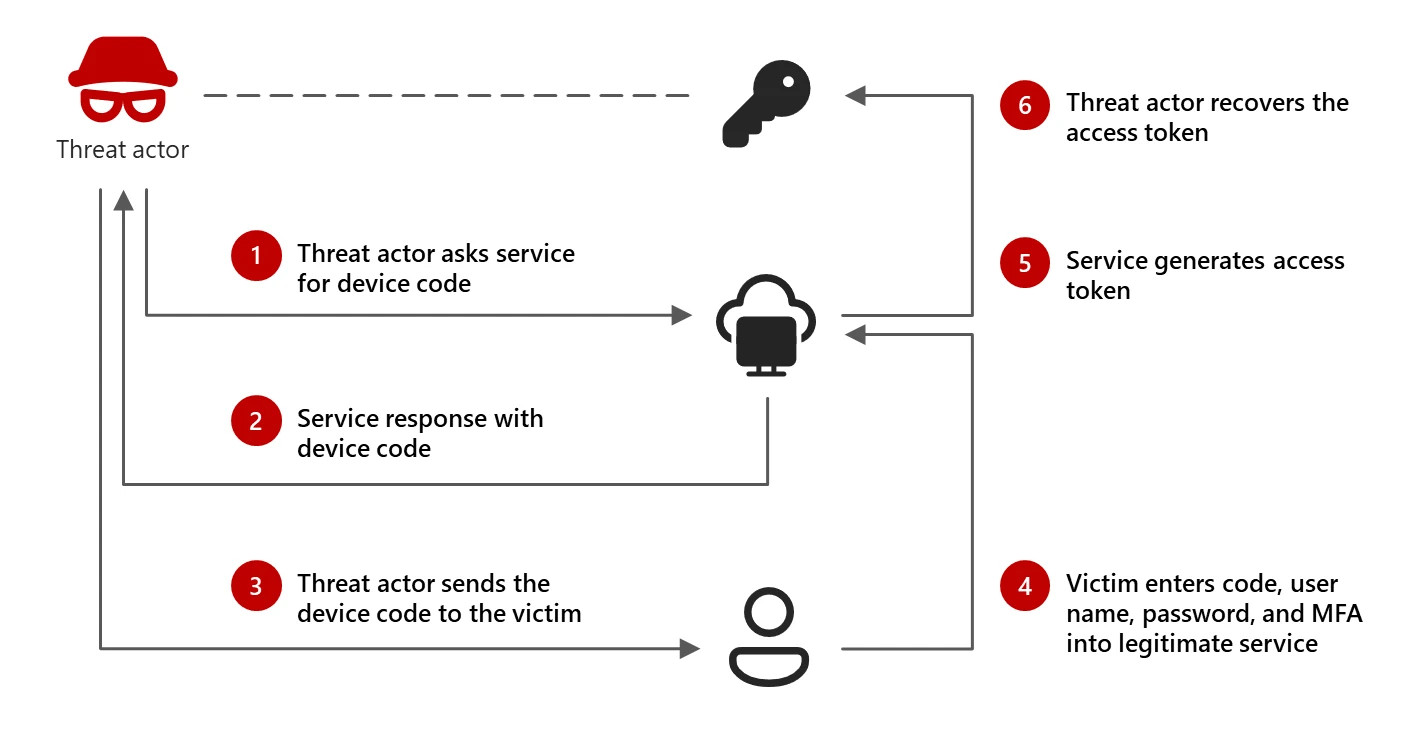
With the compromised account, the attacker can also send phishing messages to the victim’s colleagues, creating further opportunities for exploitation. Notably, Storm-2372 has been observed utilizing the specific client ID associated with Microsoft’s Authentication Broker to request additional tokens, thus enabling the attacker to register their own devices as legitimate authentication devices through Entra ID.
Protection Recommendations
To guard against the phishing tactics employed by Storm-2372, Microsoft recommends several vital protective measures:
- Disable device code flow: Where applicable, disable the device code authentication flow to minimize vulnerabilities.
- Provide phishing training: Implement regular phishing awareness training for all users to enhance their ability to recognize and respond to suspicious activity.
- Revoke access tokens: Promptly revoke access tokens when any suspicious activity related to Storm-2372 is detected using revokeSignInSessions.
- Implement risk-based sign-in policies: Establish sign-in policies based on risk levels to block access or enforce multi-factor authentication for high-risk sign-ins.
For a detailed list of defenses and mitigation strategies, one can refer to the full guidance available here.
Additional Resources
You might also like
- Check out the best password managers to enhance your security.
- Explore the best authenticator apps available for added protection.
- Stay informed about cybersecurity threats like the recent SonicWall firewall cyberattack.

Leave a comment